Details
Description
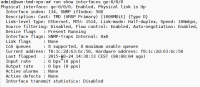
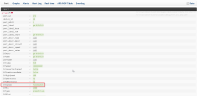
I just experienced the problem that „Alerting“ for HDX Ports does not work with JunOS, as I suspect not the real state of an interface is monitored, but something different.
Best documened by screenshots.
For Bug Fixing I can grant SNMP Access to sample devices.